Zero Trust Architecture (ZTA) has made a lot of noise in the cybersecurity world, largely due to a recent executive order issued by U.S. President Joseph Biden. In this order, Zero Trust Architecture is mentioned as one of the best practices for modernizing Federal Government cybersecurity.
What Is Zero Trust Architecture?
So just what is “Zero Trust Architecture,” or ZTA? In short, it is a method for designing the cybersecurity infrastructure of an organization’s network based on the Zero Trust security model. At its core, Zero Trust works on the principle that there is no implicit trust granted to any part of a network. Or, in layman’s terms, an organization should not trust any request without verification, irrespective of whether the request originates from inside or outside its perimeters. The Zero Trust model was developed in an effort to mitigate the potential threat of attacks on a network and increase its security posture.
Network security in general deals with access. Gaining access to a resource requires any user to prove their identity by showing credentials, thus gaining the trust of the network. The traditional “castle and moat” approach to security relies on setting up perimeter defenses where these credentials are checked and, once validated, access is granted. However, this practice creates potential security threats. For example, a single point of compromise, such as a server with outdated, legacy software could be a backdoor for the entire network. As outlined in SSL.com’s recent post, Preventing Ransomware Attacks with Digital Certificates, this is pretty much exactly what happened in the recent Darkside attack on the Colonial Pipeline:
The CEO of the company has revealed that [the attack] occurred due to an oversight. He told a Senate committee that hackers gained access through an old virtual private network that the company believed was out of commission. A CNN article from June 4, 2021 reveals that a single compromised password was all that was required to gain access to this network.
Once a malicious actor has penetrated the perimeter defense, they are free to move inside the network however they please. Moreover, credential validation only at the network’s perimeter has little to no effect on internal attacks from malicious users or compromised equipment of legitimate users.
In the Zero Trust model, every network request should be treated as if the network has already been compromised and even simple requests should be considered as a potential threat. Multi-factor authentication and authorization are required before the start of a session or any access is granted. Moreover, whenever an authenticated user is requesting access to a new resource, their credentials need to be checked again. This approach helps to restrict lateral movement once a threat is inside the network, and aids in the rapid detection, identification, and neutralization of threats, whether they come from outside or inside the network.
This shift in defense strategy is a response to modern network design trends and security requirements that include remote users, bring your own device (BYOD), and cloud-based services and devices, such as the Internet of Things (IoT). All these resources are located within the boundaries of a network, so setting a perimeter defense is no longer effective. Recent ransomware attacks highlight the need for reevaluating the security architecture of most organizations.
Many of the concepts are not new: for example, trust as a computational concept was first coined in 1994. Initially, it did not receive wide attention—mainly due to networking and security being in a relatively primitive state at that time compared to the present day. However, as technology progressed and computer networks became exponentially more complicated, defining the perimeters of an organization’s IT systems proved to be an increasingly challenging task. This led to alternative security models, such as Zero Trust, receiving traction and popularity in the industry.
NIST’s Zero Trust Roadmap
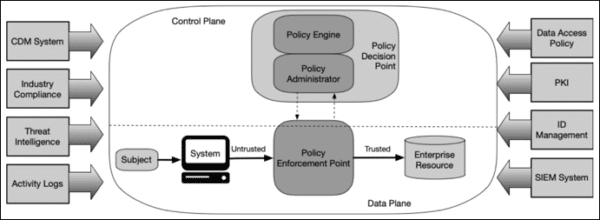
As of late 2018, the National Institute of Standards and Technology (NIST), along with the National Cyber Security Center of Excellence (NCCoE), undertook work that led to NIST Special Publication 800-207, Zero Trust Architecture. This publication provides an abstract definition of ZTA, along with a roadmap to design systems based on the principles of Zero Trust:
- All data sources and computing services are considered resources.
- All communication is secured regardless of network location.
- Access to individual organization resources is granted on a per-session basis.
- Access to resources is determined by dynamic policy—including the observable state of client identity, application/service, and the requesting asset—and may include other behavioral and environmental attributes.
- The organization monitors and measures the integrity and security posture of all owned and associated assets.
- All resource authentication and authorization are dynamic and strictly enforced before access is allowed.
- The organization collects as much information as possible about the current state of assets, network infrastructure, and communications and uses it to improve its security posture.
These tenets attempt to be technology agnostic and aim to improve an organization’s security posture. In an ideal scenario, all of these principles are taken under consideration when designing the security of a system. However, business needs vary across organizations and the exact implementation of Zero Trust Architecture should meet those requirements. The model design should be customized to the values of an organization’s resources as well as its risk appetite.
The overall goal is to prevent unauthorized access to data and services, coupled with making access control enforcement as granular as possible, while keeping overhead at a minimum. There are several ways to achieve this, but at its core, Zero Trust Architecture relies on thorough and extensive authorization and authentication mechanisms, strategically located at key security boundaries throughout the system. In this way, access is granted only to the resources that are absolutely necessary for the task at hand to be accomplished, and only to users with legitimate authority to perform them. Moreover, any deviation from normal behavior is taken under consideration when granting access. For example, access to resources outside of working hours could be considered a potential reason for denying access, depending on the organization’s modus operandi.
Moving Towards Zero Trust Architecture
Total transformation of an organization’s IT systems so as to implement Zero Trust Architecture is a complicated process. Instead, organizations should strive to continuously improve their security posture in small simple steps. Furthermore, migrating existing services to the new architecture is generally more costly than designing new services from scratch. As such, a good strategy could be to implement new services, especially cloud-based ones, in compliance with the tenets of Zero Trust (e.g. always use strong authentication methods, such as mutual TLS.)
Zero Trust is a data-centric approach, in the sense that it focuses on protecting the assets of the network rather than segments of the network themselves. A critical factor for the implementation of ZTA should be identifying the resources that require protection and the best method of safeguarding them. Data needs to be protected when at rest and in transit, thus making encryption, especially using PKI, a cornerstone of the implementation of ZTA. Collecting data regarding the efficiency of the enforced policies and user behavior is also critical in creating a dynamic system capable of adapting to the ever-changing environment that is cybersecurity.
Conclusion
Zero Trust Architecture is a modern approach to cybersecurity—a response to the latest trends and needs of the IT ecosystem as it is defined by cloud-based services to a growing degree. Although the implementation of ZTA won’t happen overnight, there are tools and solutions available at the moment that can help with the transition. Organizations looking to improve their overall security posture can benefit from existing technologies and design patterns to reevaluate their security model and move towards the latest industry best practices, such as the ZTA.
- For more information on using digital certificates as a secure, brute-force-resistant authentication factor for users and devices, please read Authenticating Users and IoT Devices with Mutual TLS.
- Hosted PKI and custom-branded issuing CAs from SSL.com offer businesses the ability to issue and manage publicly or privately trusted digital certificates without investing in PKI infrastructure and expert staffing. Our facilities and processes undergo rigorous annual external audits to maintain our WebTrust certifications and your peace of mind. For more information, please read Hosted Enterprise PKI and Subordinate CAs and Why You Might Need One.
- To speak directly with an SSL.com representative about how we can help your organization move towards Zero Trust, please email Sales@SSL.com or submit the Enterprise Sales contact form below.


