Introduction
Last week, security researchers from the University of Hamburg published a paper describing a new method that web sites could use to track browser users’ history. Their technique exploits the session resumption feature implemented in the TLS protocol.
TLS sessions
TLS is a cryptographic protocol that browsers use to secure their communications with HTTPS web servers by establishing an encrypted connection between a browser and a server. In TLS jargon, the server creates a session for each such TLS connection.
Creating a session requires additional data – such as digital certificates and encryption keys – to be exchanged before any actual web data. The process of establishing a TLS session is called the handshake negotiation
Performing a handshake for every TLS connection requires more bandwidth than unencrypted HTTP, and this is one of the major issues addressed in the recently-published TLS 1.3 protocol.
If you want to read more on the performance overhead imposed by TLS and what TLS 1.3 does to reduce it, please refer to this article.
TLS session resumption
To help alleviate the overhead associated with handshakes, TLS allows session resumption, which enables a browser to skip the handshake process with a server it has recently established a session with.
A session lasts for a predetermined period of time, from a few minutes up to several hours. If the browser revisits a server within the session window, the ongoing TLS session can resume via a single resumption request, instead of a full handshake negotiation (TLS 1.3 actually allows a browser to send application data along with the session resumption request, effectively offering the same fast performance as unencrypted HTTP.)
Tracking users with TLS session resumption
Unfortunately, in most cases security and utility are inversely proportional, and the Hamburg researchers have demonstrated that session resumption improves performance at the expense of users’ privacy.
Numerous techniques have been used to track internet users over the years, such as persistent cookies or browser fingerprinting. They are all designed to allow web sites to uniquely identify a user across visits, regardless of their IP address, location or privacy preference.
In this respect, a TLS session resumption, being uniquely tied to a specific browser, can be used to track users in the same way cookies might. Essentially, when a browser resumes a session, the web site can correlate the connection with the one that originally created the session, even if the user visits from a different network (i.e. different IP address) or with different privacy settings (e.g. user-agent).
Prolongation Attack
Using the method described above, each individual user can be tracked for (at most) several hours, based on the length of the negotiated session window.
However, a web site can renew a session for another period of time on each session resumption, resetting the session window and effectively extending the session’s lifetime indefinitely. The paper calls this technique a prolongation attack.
The researchers have demonstrated that this technique can be used to permanently track 65% of the users in their dataset, because those users tend to visit tracking web sites more often than sessions expire.
In addition, they have shown that web sites can use embedded content to track their users even across different sites. For example, an ad network that has embedded ads on millions of web sites can track individual users on all those sites. (It should be noted that some browsers, as mentioned in the paper, do block session resumption requests from third-party web sites.)
Am I vulnerable?
Protocol-wise, all TLS versions (including the latest TLS 1.3) provide a mechanism for session resumption, meaning users could be tracked using this technique, regardless of TLS version.
Additionally, out of 48 browsers tested in the paper, only 3 were found to have disabled TLS session resumption. These browsers are:
- JonDoBrowser
- Tor Browser
- Orbot (for mobile)
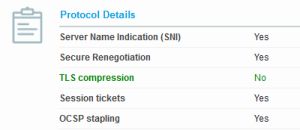
To test if your browser (or other client software) is vulnerable to this tracking technique, you can use this tool to generate a report about your client’s TLS support.
Check the “Protocol Details” section – if “Session Tickets” is set to “Yes”, then session resumption is enabled in your browser and you are traceable.
Is there a fix?
TLS session resumption tickets are stored in the browser’s TLS cache, which is destroyed every time the browser process is closed.
If you close your browser regularly and extreme privacy is not an absolute necessity, then you should be safe from this method.
Unfortunately, most modern mobile OSs keep applications “always on”, which means that it is not unusual for a browser instance to remain active for days at a time. Even though this is somewhat implausible, there are cases where it is possible for a user to be tracked in the real world.
For this reason, various privacy-oriented user groups are urging browsers to disable this feature (or at least add an option to disable it). As of this writing, however, no major browser has publicly discussed the matter.
In the meantime, if you require more privacy you can visit a web site in “incognito” or “privacy” mode. A browser using privacy mode will create a new TLS cache which will not have access to normal session resumption tickets.
Otherwise, you can temporarily switch to one of the three browsers that do not support session resumption. Alternatively, you can manually disable this feature in Firefox using the following method.
Disable session identifiers in Mozilla Firefox
Mozilla Firefox was patched in 2014 to support an undocumented option in the browser configuration to disable session resumption.
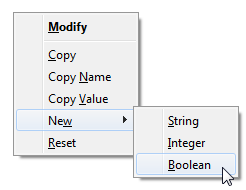
To turn session resumption off, you have to visit about:config in a Firefox (click on “I accept the risk” to proceed). Firefox will then show a list of preferences for your browser.
Right-click any preference and select “New” and “Boolean”, as shown in the following image.
A pop-up message will be shown asking for the name of the preference. Type:
security.ssl.disable_session_identifiers
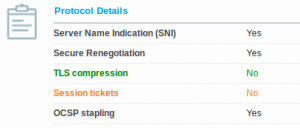
And select “true” for the value. If you did everything correctly, you should be seeing something similar to the image below.
If you now visit the SSL browser checking tool with your Firefox, it should report that “Session tickets” are disabled, meaning that you are safe from TLS session tracking.
Mozilla will start blocking all third-party trackers
Finally, Mozilla has recently announced] that they are changing their content policy. They introduced a new feature called Content Blocking in (currently latest) version 63, which allows users to block any third-party content that Firefox detects in web sites.
What’s more, in version 65 Firefox will start blocking all third-party content by default; That way users will have to give explicit permission before any external content is rendered.
Besides the tremendous improvements on user privacy, this new content blocking policy will also inadvertently reduce the security impact of the TLS session resumption technique. Although this is by no means a complete fix, web sites will only be able to track Firefox users when they actually visit them, since cross-site tracking relies on third-party content.
Conclusion
Fortunately, tracking users with TLS has been proven plausible but not practical for the majority of Internet users. Regardless, there are cases where absolute privacy is required, and while temporary solutions (such as the Firefox fix we described above) exist, we can expect appropriate mitigation from the major browser vendors soon.
As always, thanks for choosing SSL.com – where we believe a safer Internet is a better Internet.