Keeping our online accounts and personal information safe is more important than ever. With the increasing number of cyber threats, such as hacking, phishing, and data breaches, it’s crucial to protect ourselves online. One effective way to enhance the security of our online accounts is by using One-Time Passwords (OTPs). In this comprehensive guide, we’ll discuss what OTPs are, how they work, and why they are necessary to safeguard our digital lives.
What is a One-Time Password (OTP)?
A One-Time Password (OTP) is a unique password valid for only one login session or transaction. Unlike traditional passwords that remain static until manually changed by the user, OTPs automatically change every time they are used. Even if an attacker obtains an OTP, it will be useless for future login attempts, as a new OTP will be required. This added layer of security makes it much harder for hackers to gain unauthorized access to your accounts, even if they have your regular password.
How OTPs Work
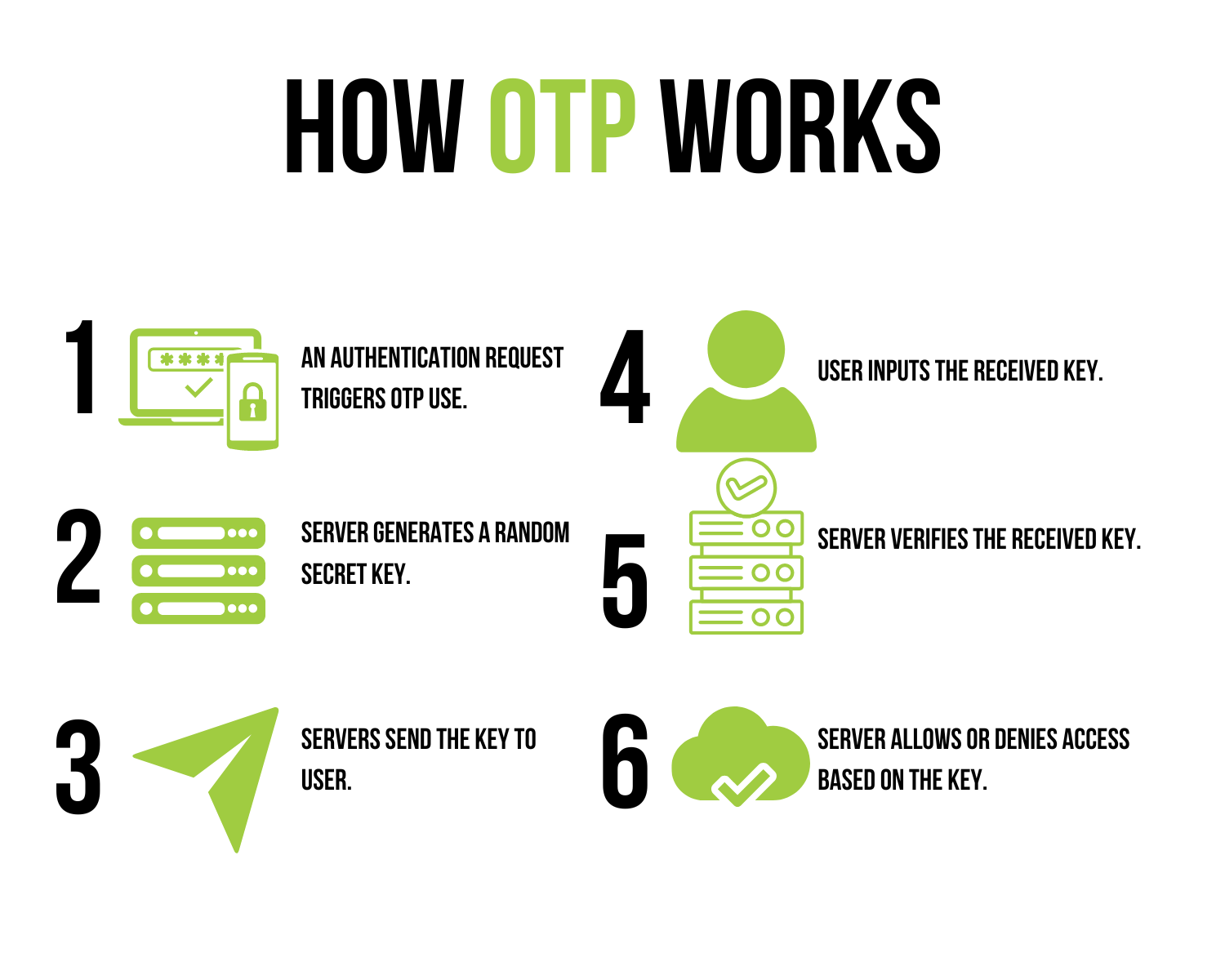
OTPs are generated by special algorithms that create a new, unique password for each login attempt. These algorithms use various factors to generate the OTP, such as:
- A secret key is a unique code known only to you and the service you’re logging into. It serves as the basis for generating the OTP.
- A counter or timestamp: HOTPs (HMAC-based One-Time Passwords) use a counter that increments each time an OTP is generated, while TOTPs (Time-based One-Time Passwords) use the current time as a factor.
- A cryptographic hash function: This complex mathematical function takes the secret key and counter or timestamp as input and generates a unique OTP.
When you attempt to log into a service that uses OTPs, the algorithm generates an OTP based on these factors. The service also runs the same algorithm and compares the generated OTP with your provided one. If they match, you are granted access to your account. Once the OTP is used or after a short period (usually 30 seconds for TOTPs), the OTP expires and can no longer be used for authentication.
Types of OTPs
There are two main types of OTPs:
- HOTP (HMAC-based One-Time Password): HOTPs generate OTPs using a secret key and a counter. Each time an OTP is generated, the counter increments by one, ensuring that the same OTP is never used twice. HOTPs are often used with hardware tokens, which are small devices that generate OTPs at the push of a button.
- TOTP (Time-based One-Time Password): TOTPs generate OTPs using a secret key and the current time. The OTP is only valid for a short time window, usually 30 seconds, after which a new one is generated. TOTPs are commonly used with mobile apps, such as Google Authenticator or Authy, which generate OTPs on your smartphone.
Why OTPs are Important
OTPs offer several significant advantages over traditional static passwords:
- Enhanced Security: Because OTPs change with every login attempt, they are much more difficult for hackers to guess or steal than static passwords. Even if a hacker obtains an OTP, it will be useless for future login attempts, significantly reducing the risk of unauthorized access to your accounts.
- Protection Against Phishing and Man-in-the-Middle Attacks: Phishing attacks involve tricking users into revealing their login credentials, often by creating fake login pages that look identical to legitimate ones. Man-in-the-Middle (MITM) attacks involve intercepting the communication between a user and a service, allowing the attacker to steal login information. OTPs help protect against these attacks because even if a user accidentally reveals their OTP or is intercepted, the OTP will expire before the attacker can use it, rendering the attack ineffective.
- Compliance with Industry Standards: Many industries, such as finance and healthcare, have strict security regulations that require strong authentication measures to protect sensitive data. OTPs help businesses comply with these standards, such as the Payment Card Industry Data Security Standard (PCI-DSS) and the Health Insurance Portability and Accountability Act (HIPAA), by providing an additional layer of security beyond simple passwords.
How OTPs are Generated
OTPs are generated using standardized cryptographic algorithms that ensure the generated passwords are secure and cannot be easily guessed or reverse-engineered. The two most common algorithms used for OTP generation are:
- HMAC-SHA1 for HOTPs: This algorithm uses a secret key and a counter value as input, along with the SHA-1 (Secure Hash Algorithm 1) hash function, to generate a unique OTP.
- SHA-1 or SHA-256 for TOTPs: These algorithms use a secret key and the current timestamp as input, along with the SHA-1 or SHA-256 hash functions, respectively, to generate a unique OTP.
These algorithms are designed to be computationally infeasible to reverse, meaning that even if an attacker knows the OTP, they cannot determine the secret key or predict future OTPs. When used with secure communication channels, such as those protected by SSL/TLS encryption, OTPs provide a robust, multi-layered security solution that significantly reduces the risk of unauthorized access to sensitive data.
Real-World Applications of OTPs
OTPs are widely used across various industries to secure online accounts, transactions, and sensitive data. Some common examples include:
- Online Banking and Financial Services: Banks and financial institutions use OTPs to secure online banking sessions, verify transactions, and prevent fraud. When you log into your online banking account or make a transaction, you may be required to enter an OTP sent to your mobile device to confirm your identity.
- E-commerce and Online Shopping: Online retailers use OTPs to secure user accounts and prevent unauthorized purchases. When you purchase or change account details, you may be asked to enter an OTP to verify your identity and ensure the transaction is legitimate.
- Healthcare and Medical Services: Healthcare providers use OTPs to secure access to sensitive patient data and comply with HIPAA regulations. When healthcare professionals access patient records or share sensitive information, they may be required to enter an OTP to authenticate their identity and ensure that only authorized individuals can view the data.
- Corporate and Enterprise Security: Businesses use OTPs to secure employee access to company networks, applications, and data. Employees may be required to use OTPs in addition to their regular passwords when logging into company systems or accessing sensitive information, helping to prevent unauthorized access and data breaches.
User Experience and Convenience
One of the critical challenges in implementing OTPs is ensuring that the process is user-friendly and convenient while still providing robust security. To address this, many OTP solutions are designed with ease of use in mind, offering multiple ways for users to receive and enter OTPs, such as:
- Mobile Apps: OTP mobile apps, such as Google Authenticator or Microsoft Authenticator, allow users to generate smartphone OTPs. These apps are easy to set up and use and provide a convenient way for users to access OTPs whenever needed.
- SMS Text Messages: Some services send OTPs to users via SMS text messages. This approach is convenient for users who may not have a smartphone or prefer not to use mobile apps. However, SMS-based OTPs can be vulnerable to interception and are generally less secure than app-based OTPs.
- Hardware Tokens: Hardware tokens are small devices that generate OTPs at the push of a button. They are often used in corporate and enterprise settings where high-security levels are required. While hardware tokens offer robust security, they can be less convenient for users, as they must carry the token with them and remember to use it whenever they log in.
To further enhance user experience, many OTP solutions offer additional features, such as:
- Backup Codes: Some services provide users with one-time backup codes that can be used if they lose access to their primary OTP method (e.g., if their phone is lost or stolen). These backup codes can be printed or stored securely as a fallback authentication method.
- Multi-Device Support: Many OTP solutions allow users to set up multiple devices, such as smartphones and tablets, to generate and receive OTPs. This feature ensures users can always access their OTPs, even if one device is lost or damaged.
- Biometric Authentication: Some OTP solutions incorporate biometric authentication, such as fingerprint scanning or facial recognition, as an additional factor for generating or accessing OTPs. This approach combines the security of OTPs with the convenience and ease of use of biometric authentication.
- The Future of OTPs
As cyber threats continue to evolve and become more sophisticated, the importance of strong authentication measures like OTPs will only continue to grow. In the future, we can expect to see further innovations in OTP technology, such as:
- Integration with Biometric Factors: As mentioned earlier, incorporating biometric authentication into OTP solutions can provide an additional security layer while improving user experience. As biometric technologies become more advanced and reliable, we may see widespread adoption of biometric-based OTPs.
- Advancements in Cryptographic Algorithms: As computing power increases and new threats emerge, the cryptographic algorithms used to generate OTPs will continue to evolve to stay ahead of potential attacks. This may involve developing new, more secure algorithms or adopting quantum-resistant cryptography to protect against the threat of quantum computing.
- Increased Adoption of Hardware-based Security: Hardware-based security solutions, such as hardware tokens or embedded secure elements in smartphones, offer higher protection against software-based attacks. As the cost and complexity of these solutions decrease, we may see more widespread adoption of hardware-based OTPs in both consumer and enterprise settings.
- Integration with Other Security Technologies: OTPs can be combined with other security technologies, such as risk-based or contextual authentication, to create even more robust and adaptive security solutions. These integrated approaches can consider factors such as the user’s location, device, and behavior to determine the appropriate level of authentication required for a given situation.
Conclusion
One-time passwords (OTPs) are a critical component of cybersecurity, providing additional protection against unauthorized access, phishing attacks, and data breaches. Businesses and individuals can make informed decisions about implementing this essential security measure by understanding how OTPs work, their benefits, and their real-world applications.
As our reliance on digital services continues to grow, the importance of strong authentication measures like OTPs will only increase. By staying informed about the latest developments in OTP technology and adopting best practices for implementation and use, we can all contribute to creating a more secure digital future.
Remember, while OTPs are a powerful tool for enhancing online security, they are just one piece of the cybersecurity puzzle. To create a comprehensive and effective cybersecurity strategy, OTPs must be used in conjunction with other security best practices, such as strong passwords, regular software updates, and employee security awareness training.
< p class=”md-end-block md-p md-focus”>By taking a proactive approach to cybersecurity and embracing solutions like OTPs, we can all work together to create a safer and more secure online environment for everyone.

