Public Key Infrastructure, commonly abbreviated as PKI, has become a core component of securing online communications and transactions. But what exactly constitutes this critical security framework?
At its essence, a Public Key Infrastructure refers to policies, procedures, technologies, and components facilitating the secure electronic transfer of information, transactions, and communications between entities like individuals, devices, and systems. It aims to achieve this through cryptographic mechanisms to ensure confidentiality, integrity, authentication, and non-repudiation.
The central premise relies on , particularly public key encryption, based on a mathematically linked cryptographic key pair—a private key and a public key. These keys encrypt and decrypt data in a way that only the other corresponding key can access the content. More on this later. First, let’s examine the core components that constitute a complete PKI system.
The Main Components of a PKI Ecosystem
A functional PKI has a combination of technical, organizational, and procedural elements.
Certificate Authorities (CAs)
CAs form the foundation of PKI. They issue, revoke, and renew digital identity certificates. A digital certificate contains information about an entity alongside its public key. Essentially, the digital certificate binds a cryptographic key pair used to encrypt communication to a validated identity that the key pair belongs to. The CAs, such as SSL.com, extensively verify the details before digitally signing these certificates for distribution.
A certificate and the CA that issues it are trusted by the users and systems that rely on the certificates for secure communication. This introduces trust as recipients recognize a reputable CA has validated the certificate holder.
Trust of Certificate Authorities and Certificates
The concept of “trust” in the context of Certificate Authorities revolves around the assurance that a given digital certificate is legitimate and that the entity presenting the certificate is who they claim to be. This trust framework is crucial for secure communications on the internet, especially for activities like online banking, shopping, and confidential communications, where verifying the authenticity of a website or service is essential.
Public Trust
Public trust involves certificates issued by CAs that are widely recognized and automatically trusted by major browser companies, software developers, and operating systems. This trust is established because the CA follows strict policies and procedures before issuing a certificate, ensuring the entity requesting the certificate is legitimate and has the right to use the domain in question, apply a digital signature with a specific name, or otherwise represent an identity attached to a cryptographic function.
Public trust stems from the guidelines and requirements set by a standards body called the Certificate Authority Browser Forum or CA/Browser Forum. The CA/Browser Forum is a voluntary consortium of certification authorities, internet browser vendors, and other interested parties who develop guidelines that govern the issuance and management of these publicly trusted certificates. Major browser companies and operating systems decide which CAs they trust and include these in their trusted root certificate stores. If a CA is not in this trust store, users might receive warnings that the certificate is not trusted.
Private Trust
Private trust involves certificates issued within a closed ecosystem, such as a corporate intranet or a controlled environment where the entities involved have a direct relationship or trust with each other. In these scenarios, an organization might act as its own CA (Private CA) and issue certificates to its users, devices, or services. These certificates are not necessarily recognized by the outside world but are fully valid within the organization’s ecosystem.
Delineation Between Public and Private Trust
The primary delineation between public and private trust lies in the scope and recognition of the issued certificates. Publicly trusted CAs have their root certificates included in the trusted stores of major browsers and operating systems, enabling their issued certificates to be automatically trusted by a wide audience without any additional configuration.
In contrast, certificates issued by a private CA require manual trust configuration in any systems outside the private network that wish to trust those certificates. These are not automatically trusted by the broader internet and are mainly used for internal purposes where the organization has control over the trusting parties.
Both public and private trust models play crucial roles in internet security and the internal security of organizations, each serving different needs based on the scope of trust and recognition required.
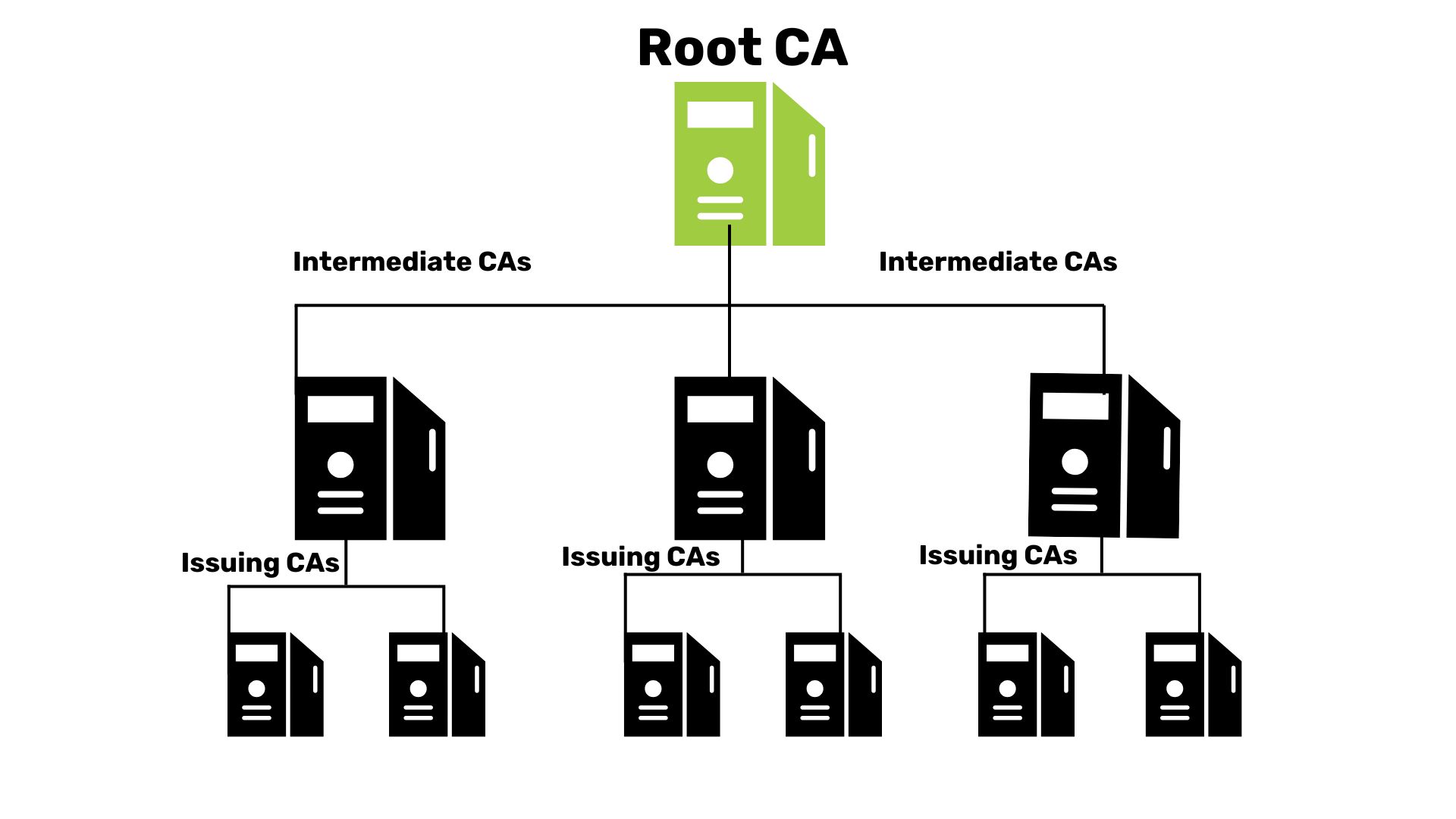
PKI Hierarchy
CAs come in two categories. Root CAs form the peak of the hierarchy, while intermediate CAs distribute certificates under them.
Registration Authorities (RAs)
RAs verify identity and establish the enrollment process before requesting signed certificates from CAs accordingly. RAs ensure only legitimate entities receive certificates per PKI policy guidelines. The extensive identity checks before certificate generation enhance trust among stakeholders.
Public and Private Cryptographic Keys
This mathematically linked pair enables the inner cryptographic workings of PKI. Data encrypted with the public key remains inaccessible without the corresponding private key for decryption. This maintains confidential data during transmissions. Digital signatures signed with a private key can be verified with the corresponding public key for identity authentication.
To understand the different types of PKI implementations and which might be right for your organization, check out our guide on .
Digital Certificates
The digital certificate contains identifying details like name, organization, location, and the associated public key. The certificate also bears the digital signature of the issuing CA for assurances around the bound identity. Certificates comply with X.509 international standards to enable interoperability across systems.
Certificate Revocation List (CRL)
The CRL contains a list of certificate serial numbers revoked by respective CAs indicating compromised identities. Entities crosscheck CRLs to ensure they only communicate with certificates still within validity. This centralized reference list facilitates efficient revocation distribution.
For more information about how certificate revocation works and how organizations maintain their security, see our comprehensive guide to .
What is PKI Used For?
PKI is not just a theoretical framework—it enables several commonplace technologies:
- Secure Web Activity: HTTPS, SSL/TLS protocols establishing secure connections between browsers and servers utilize PKI for the underlying encryption powered by digital certificates and public-key cryptography.
- Email Encryption and Signing: Sensitive information exchange over emails leverages PKI standards through certificate types like S/MIME (Secure/Multipurpose Internet Mail Extensions) to encrypt and sign emails.
- Code Signing Certificates: Applies a cryptographic signature to software code that seals it against unauthorized changes and identifies the publisher.
- Authentication and Access Control: Certificate-based authentication mechanisms for enterprise VPN access and building entry systems provide far more robust security over ID-password protocols through PKI methodologies.
- Blockchain Transactions: All transactions on blockchain ledgers involve digital currency transfer by signing through asymmetric cryptography keys enabled by PKI principles around mathematical linkage between keys.
As digital connectivity grows globally across industries, PKI will remain a foundational element enabling privacy, trust, and security through existing standards around certificates, identity management, and encryption.
How Does PKI Work?
- Key Pair Generation: Each entity creates a public and private key pair.
- Certificate Issuance: A trusted Certificate Authority (CA) verifies the entity’s identity and issues a digital certificate containing the public key.
- Distribution: Public keys and certificates are distributed, while private keys remain secret and should be kept safe by the certificate holder.
- Encryption: Senders use the recipient’s public key to encrypt messages.
- Decryption: Recipients use their private key to decrypt messages.
- Digital Signatures: Senders sign messages with their private key, verifiable by others using the sender’s public key.
- Certificate Validation: Entities verify certificates using the CA’s public key before trusting them.
This system enables secure communication, authentication, and non-repudiation in digital environments.
The Importance of PKI
At SSL.com, we have seen firsthand the immense value PKI delivers in securing sensitive data transmission. As a leading publicly trusted certificate authority, we remain committed to advancing PKI standards through robust identity verification, rapid certificate issuance, and proactive infrastructure monitoring.