Digital certificates from SSL.com can be an important part of a health care organization’s plans for HIPAA-compliant email, authentication, and websites.
HIPAA Breaches and Penalties
The U.S. Health Insurance Portability and Accountability Act (HIPAA), initially passed in 1996, protects the security and privacy of patients’ Electronic Protected Health Information (also known as PHI or ePHI). HIPAA compliance is enforced by the Office for Civil Rights (OCR) of the U.S. Department of Health and Human Services (DHS).
For 2020, legal journalist Steve Alder reports on HIPAA Journal that 642 large-scale data breaches were reported by health care institutions including healthcare providers and healthcare clearing houses. This statistic is 25% bigger compared to 2019 which itself was already a record-breaking year.
Compared to year 2020, health care data breaches have tripled since 2010, and doubled since 2014. There has therefore been a 25% yearly increase of data breaches. Over-all, a staggering 78 million healthcare records have been breached between 2009-2020.
Major Reasons for Healthcare Data Breaches in 2020
The five major causes of healthcare data breaches in 2020 were identified: hacking/IT incident (26.9 million records breached), unauthorized access/disclosure (787,015 records breached), theft (806,552 records breached), improper disposal (584,980 records breached), and loss (169,509 records breached).
Clearly, cybersecurity attacks comprised the biggest reason for healthcare data being stolen. The cyber attacks included the all-too-common phishing, sending malware, exploitation of vulnerabilities, and ransomware.
In the latter months of 2020, incidences of ransomware increased significantly. Check Point reported that health care was the most targeted industry, by ransomware attackers, in October 2020. The Ryuk ransomware gang was one of the most notorious that month. They took out the computer systems of Sky Lakes Medical Center and forced clinicians to resort to handwriting to document patient information. They also attacked University of Vermont Health Network wherein up to 20 medical facilities were victimized.
It is also theorized that Ryuk was responsible for the ransomware attack against Universal Health Services (UHS) which has 400 hospitals in the US and annually caters to millions of patients. UHS is estimated to have lost $67 million for damages including lost revenue due to ambulances being redirected to other hospitals, more than a 2-month delay in billing procedures, and gigantic expenses to fix their systems.
Between October and September of 2020, an alarming 71% increase in ransomware attacks was observed. Ransomware cases in 2020 comprised several of the most injurious cyber attacks that occurred against health care organizations that year. In a lot of these attacks, systems were blacked out for many weeks and as a result, patient services were severely impacted.
Digital Certificates for Information Protection and Authentication
HIPAA’s section on technical safeguards makes it clear that patients’ PHI must be protected by health care providers when transmitted over a computer network or at rest. Relevant regulations include (but are not limited to):
164.312 (a)(2)(iv): Encryption and decryption (Addressable). Implement a mechanism to encrypt and decrypt electronic protected health information.
164.312 (c)(1): Standard: Integrity. Implement policies and procedures to protect electronic protected health information from improper alteration or destruction.
164.312 (d): Standard: Person or entity authentication. Implement procedures to verify that a person or entity seeking access to electronic protected health information is the one claimed.
164.312 (e)(1): Standard: Transmission security. Implement technical security measures to guard against unauthorized access to electronic protected health information that is being transmitted over an electronic communications network.
Because it was intended to be “future-proof,” HIPAA doesn’t spell out the exact technologies that must be used to protect PHI. Today, digital certificates offered by publicly trusted certificate authorities (CAs), like SSL.com, offer a great solution for ensuring the encryption, authentication, and integrity of digital communications.
We’ll cover three important applications of digital certificates for HIPAA-compliant communication here: S/MIME certificates for secure email, certificate-based client authentication, and SSL/TLS certificates for protecting websites and web applications. We’ll also discuss how SSL.com’s advanced certificate management tools can help you plan and maintain coverage for your entire organization and keep your certificates up-to-date.
S/MIME Email and Client Authentication for HIPAA Compliance
Email has been in use for communication over computer networks since the early 1970s, and is insecure by default. Email is based on plaintext protocols, provides no way to ensure the integrity of messages, and includes no mechanism for robust authentication. S/MIME (Secure/Multipurpose Internet Mail Extensions) certificates from SSL.com can solve these issues by ensuring encryption, authentication and integrity for your organization’s email:
- Encryption: S/MIME provides robust end-to-end encryption so that messages cannot be intercepted and read in transit. For example, S/MIME can protect messages sent over the internet, between offices or organizations and outside of any company firewalls.
- S/MIME encryption is aysmmetric, with both public and private keys. Anyone with a recipient’s public key can send them an encrypted message, but only a person in posession of the corresponding private key can decrypt and read it. Therefore, it is safe to distribute public keys both within and outside of an organization, while private keys must be kept secure.
- Authentication: Each S/MIME email message is signed with a unique private key associated with the email address (and optionally the individual person and/or organization) that sent it. Because the sender’s identity has been verified by a trusted third-party CA—such as SSL.com—and bound to this secret key, recipients are assured of the true identity of the sender.
- Integrity: Each signed S/MIME email message includes an encypted hash (a type of digital “fingerprint” or checksum) of the message’s contents that can be independently calculated and confirmed by the recipient’s email software. If a message is somehow intercepted and altered (even by one character) the computed hash value will not match the digital signature. This means that recipients of digitally signed email can be certain of a message’s integrity.
Furthermore, because a trusted digital signature ensures the authenticity and integrity of email, S/MIME provides legal non-repudiation for email messages; it is difficult for a sender to plausibly deny that they sent that exact message.
HIPAA Compliance for Email in Transit and at Rest
S/MIME certificates from SSL.com can provide HIPAA compliance for an organization’s email while in transit or at rest:
- In transit: The integrity and authenticity of S/MIME email is ensured by a unique, trusted digital signature. End-to-end encryption ensures that messages cannot be read by a third party when transmitted over insecure networks (such as the internet).
- At rest: S/MIME encryption ensures that only someone in possession of the recipient’s private key can decrypt and read messages encrypted with their public key. Encrypted email stolen in data breaches or otherwise compromised is useless to attackers without access to these keys.
Client Authentication
All S/MIME certificates issued by SSL.com include client authentication. Client authentication certificates can be used as an authentication factor for access to protected network resources, such as VPNs and web applications where patients’ PHI is handled. Therefore, S/MIME and client certificates from SSL.com can be distributed to personnel as a unified solution for:
- Authentication for access to protected health information.
- Encryption, authentication, and integrity of email in transit or at rest.
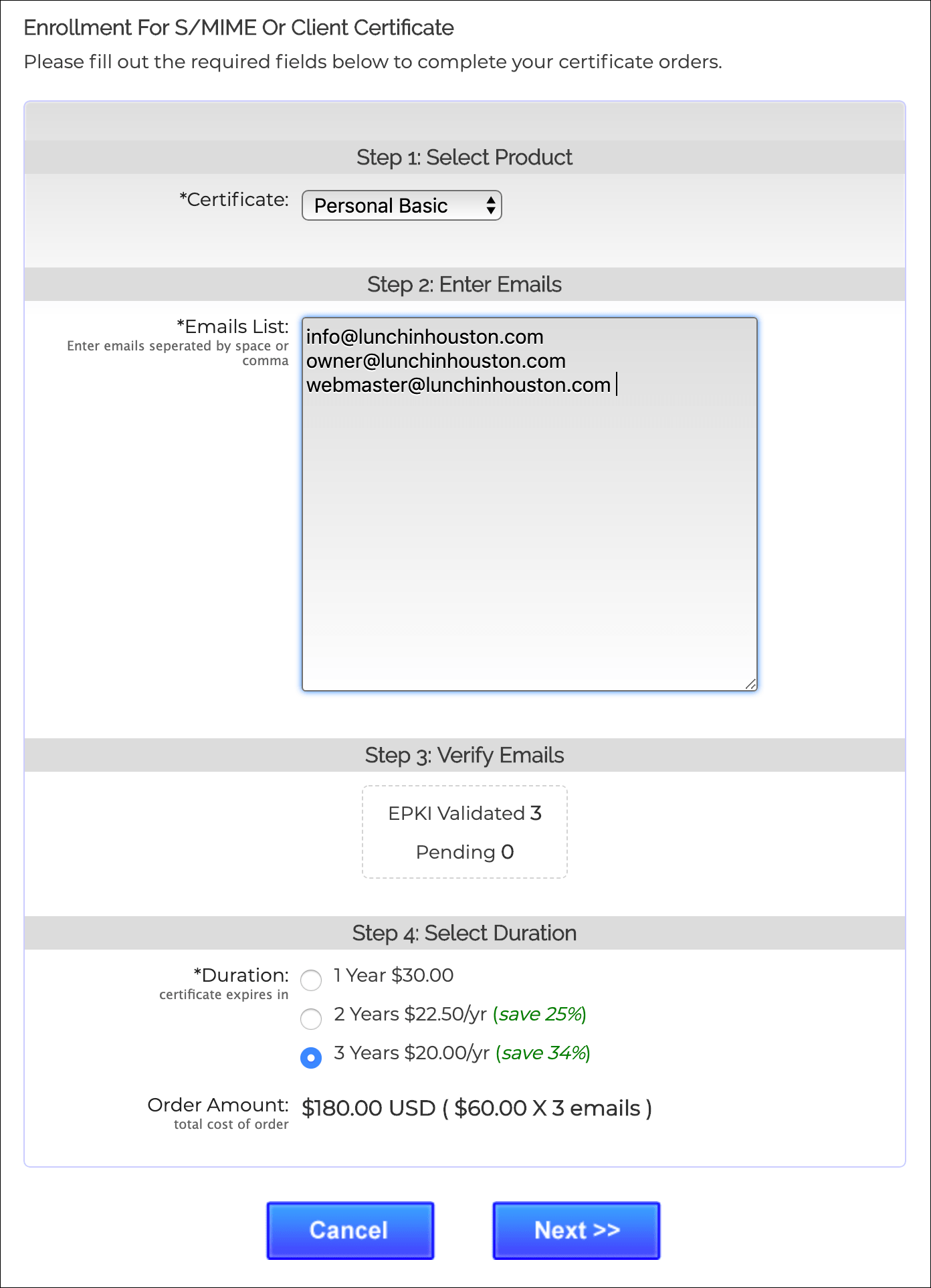
Bulk S/MIME Certificates Enrollment
Using S/MIME certificates for HIPAA compliance requires a plan for issuing certificates to all personnel working with PHI and managing these certificates over time. Employees come and go, certificates expire, and certificates may need to be revoked for various reasons, including private key compromise.
Health care providers can easily issue S/MIME certificates in bulk from SSL.com’s advanced customer account portal. These certificates may be managed, renewed, and revoked as necessary.
Organizations requiring a large number of certificates may also benefit from wholesale discounts of up to 65% by participating in SSL.com’s Reseller and Volume Purchasing Program.
SSL/TLS for Website Security
In 2021, all websites should be protected with an SSL/TLS certificate and use the HTTPS protocol, but it’s an absolute must for for any website or web application required to be HIPAA compliant. Like S/MIME for email, the SSL/TLS protocol provides encryption, authenticity, and integrity for websites:
- All communications between a website protected with a properly configured SSL/TLS certificate and a web browser are securely encrypted.
- The identity of an HTTPS website presenting a valid certificate signed by a publicly trusted CA will be accepted by web browsers and made available to users.
- Depending on the level of validation chosen by its owner, a website’s SSL/TLS certificate may simply indicate that a CA has confirmed control of a website by the certificate applicant, or it may include detailed information about the entity operating the site, such as a company or other organization.
- For maximum trust, healthcare organizations may wish to invest in High Assurance (OV) or Extended Validation (EV) certificates, providing proof of identity to users.
- Documents—such as web pages—from an HTTPS website protected by an SSL/TLS certificate have their integrity guaranteed by an encrypted hash included in the digital signature, which is independently calculated by the browser before trusting the document. The data cannot be intercepted and altered by a malicious third party while in transit without the browser detecting the error and warning the user.
Expiration Reminders and Automation
All certificates have an expiration date, after which they will not be trusted by client software. For publicly trusted SSL/TLS, the maximum certificate lifetime is currently 398 days. If you let a website’s SSL/TLS certificate expire, browsers will no longer trust it:
It can be difficult to keep track of expiring certificates and keep them updated, and current certificates are crucial to maintaining secure, HIPAA-complient websites. SSL.com provides several powerful options for making sure your certificates are up to date:
- Expiration reminders: SSL.com provides configurable notices to remind you when it’s time for a certificate to be renewed. This is a great option for organizations with a small number of certificates, or in situations where automation is inconvenient or impossible due to technical constraints.
- Scripting and automation: Organizations can create custom scripts leveraging SSL.com’s RESTful SWS API or the industry-standard ACME protocol to automate SSL/TLS certificate renewal, eliminating the need for reminders. Automation is especially important if a organization has a large number of servers and certificates to maintain.
SSL.com provides a wide variety of SSL/TLS server certificates for HTTPS websites, including:
Conclusion
We hope this post has helped you understand how digital certificates can be a part of your organization’s plan for HIPAA compliance, and how SSL.com’s advanced management tools can help you make sure your organization is protected and up-to-date.
If you have any questions about purchasing certificates for your organization especially for bulk issuance of S/MIME Certificates, please contact SSL.com’s enterprise sales team via the form below. You can also contact SSL.com support by email at Support@SSL.com, by phone at 1-877-SSL-SECURE, or by clicking the chat link at the bottom right of this page.
And, as always, thank you for visiting SSL.com, where we believe a safer internet is a better internet!
Contact SSL.com Enterprise Sales