New from SSL.com: Preparing for 45-Day SSL/TLS Certificates
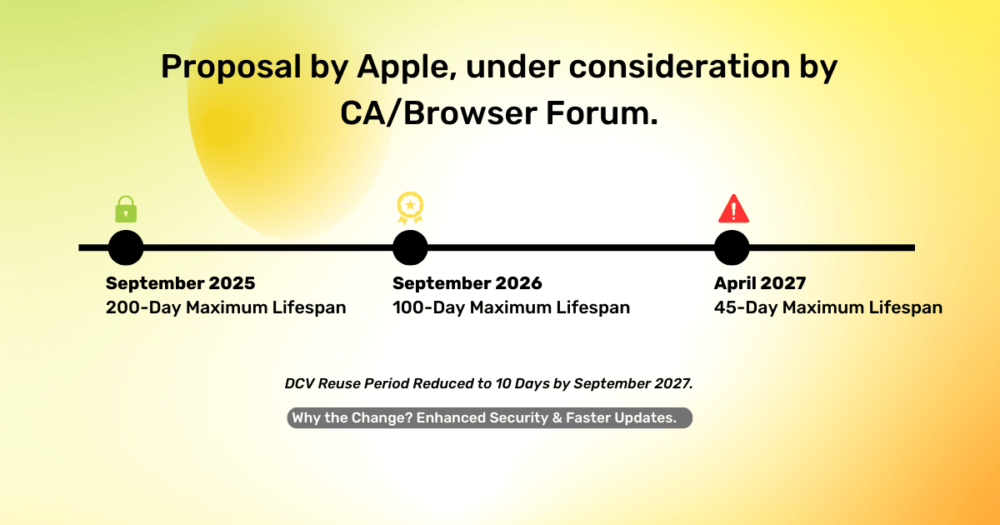 Apple’s push for 45-day SSL/TLS certificates, supported by Google’s move to 90-day lifespans, emphasizes enhanced security but brings challenges like frequent renewals and error risks. SSL.com offers automation solutions, including ACME protocol support and APIs, to simplify certificate management and help organizations adapt seamlessly. By leveraging these tools and educating teams, businesses can turn this shift into an opportunity to strengthen their cybersecurity posture. Read the full article on SSL.com to learn how we can help you navigate these changes.
Apple’s push for 45-day SSL/TLS certificates, supported by Google’s move to 90-day lifespans, emphasizes enhanced security but brings challenges like frequent renewals and error risks. SSL.com offers automation solutions, including ACME protocol support and APIs, to simplify certificate management and help organizations adapt seamlessly. By leveraging these tools and educating teams, businesses can turn this shift into an opportunity to strengthen their cybersecurity posture. Read the full article on SSL.com to learn how we can help you navigate these changes.
Cyber Security Alert: T-Mobile Blocks Critical Network Threat
 A Chinese hacking group known as “Salt Typhoon” attempted to breach T-Mobile’s network through a wireline provider, but the attack was successfully blocked with no customer data compromised. Federal authorities are investigating similar attacks against other major U.S. telecom providers like AT&T and Verizon as part of what appears to be a coordinated cyber espionage campaign. The FBI and CISA have launched investigations into these incidents, while T-Mobile’s successful defense highlights the importance of strong network security measures.
A Chinese hacking group known as “Salt Typhoon” attempted to breach T-Mobile’s network through a wireline provider, but the attack was successfully blocked with no customer data compromised. Federal authorities are investigating similar attacks against other major U.S. telecom providers like AT&T and Verizon as part of what appears to be a coordinated cyber espionage campaign. The FBI and CISA have launched investigations into these incidents, while T-Mobile’s successful defense highlights the importance of strong network security measures.
Defending against sophisticated cyberattacks demands proactive strategies to secure sensitive communications and systems.
- Segment and monitor network connections to identify and isolate compromised systems quickly.
- Encrypt data at all transfer points to prevent unauthorized access, even if breached.
- Strengthen endpoint security to limit exposure to cyberespionage operations targeting sensitive information.
SSL.com’s Client Authentication Certificates provide a critical layer of protection by verifying access, ensuring that only trusted entities can interact with critical systems. This shields sensitive data from unauthorized actors and reduces reliance on passwords alone.
Fortify Your Systems with Confidence
Supply Chain Security Alert: Blue Yonder Ransomware Impact
 A ransomware attack on supply chain software provider Blue Yonder has disrupted operations for major retailers including Starbucks, Morrisons, and Sainsbury’s by compromising warehouse management and scheduling systems. While Starbucks and Sainsbury’s have restored their systems, Morrisons remains on backup operations as cybersecurity teams work to recover from the attack. The incident highlights the vulnerability of global supply chains to cyber threats and their potential for widespread operational impact.
A ransomware attack on supply chain software provider Blue Yonder has disrupted operations for major retailers including Starbucks, Morrisons, and Sainsbury’s by compromising warehouse management and scheduling systems. While Starbucks and Sainsbury’s have restored their systems, Morrisons remains on backup operations as cybersecurity teams work to recover from the attack. The incident highlights the vulnerability of global supply chains to cyber threats and their potential for widespread operational impact.
Safeguarding against supply chain ransomware requires robust security measures and proactive defenses.
- Require strong authentication for access to critical systems, minimizing the risk of unauthorized entry.
- Implement regular vulnerability assessments to identify and patch weaknesses in third-party connections.
- Ensure real-time monitoring of system activities to detect and respond to suspicious behavior immediately.
SSL.com’s EV Code Signing certificates provide an unparalleled level of trust by verifying the integrity and authenticity of software code, especially those in CI/CD pipelines. They prevent tampering and provide assurance that your applications are safe and unaltered by malware.
Secure Your Code Against Threats
Mobile Security Alert: SpyLoan Apps Infect 8M Android Devices
 McAfee researchers discovered 15 malicious loan apps that have infected about 8 million Android devices, representing a 75% increase in infections during Q2-Q3 2024. These SpyLoan apps use deceptive tactics like fake reviews to steal sensitive data, with some variants persisting on app stores despite Google’s removal efforts. Users are advised to remove these apps immediately and exercise caution when installing financial apps, while reporting any incidents to authorities and Google.
McAfee researchers discovered 15 malicious loan apps that have infected about 8 million Android devices, representing a 75% increase in infections during Q2-Q3 2024. These SpyLoan apps use deceptive tactics like fake reviews to steal sensitive data, with some variants persisting on app stores despite Google’s removal efforts. Users are advised to remove these apps immediately and exercise caution when installing financial apps, while reporting any incidents to authorities and Google.
The rise of malicious apps poses a significant cybersecurity challenge for smartphone users worldwide.
- Scrutinize app developers’ credentials and reviews before downloading to avoid untrusted sources.
- Limit app permissions to only what’s necessary and monitor them regularly for changes.
- Keep devices updated with the latest security patches to mitigate vulnerabilities.
Adopting robust cybersecurity practices, including encrypting sensitive communication and data with trusted certificates, ensures an additional layer of protection against malicious threats.
Global Cybersecurity Roundup: Critical Developments in Data Protection
 The US Justice Department has implemented new regulations limiting foreign access to American data, specifically targeting six nations including China and Russia, as cybercrime losses hit $12.5 billion in 2023. Mexico has become Latin America’s primary cyber target with 31 billion attempted attacks in early 2024, while India faces projections of nearly 1 trillion annual cyberattacks by 2033. The global cyber landscape continues to evolve with the UK sanctioning Russian cybercrime group members and Microsoft warning of Iranian election infrastructure threats, as phishing remains the leading attack vector.
The US Justice Department has implemented new regulations limiting foreign access to American data, specifically targeting six nations including China and Russia, as cybercrime losses hit $12.5 billion in 2023. Mexico has become Latin America’s primary cyber target with 31 billion attempted attacks in early 2024, while India faces projections of nearly 1 trillion annual cyberattacks by 2033. The global cyber landscape continues to evolve with the UK sanctioning Russian cybercrime group members and Microsoft warning of Iranian election infrastructure threats, as phishing remains the leading attack vector.
Emerging cybersecurity developments underline the critical need for proactive measures to safeguard sensitive data.
- Enforce strict data access policies to prevent unauthorized foreign access to critical information.
- Use encryption protocols to secure data during transfer and storage, limiting potential exposure.
- Implement robust threat detection systems to monitor and respond to phishing and other cyberattacks.


