For many of us, the idea of preventing a cyberattack or avoiding malware can be stress-inducing. After all, though most of us now live increasingly online, few of us have formal training on the subject. But one of the most common types of attacks, phishing, is easy to prevent if you know what to look for.
Phishing scams rely on their targets willingly handing over sensitive information (like passwords or credit card numbers), or installing malware on their device. This is done by duping people through the use of fake email messages and websites. Usually, it begins with an email that purports to be from a trusted source and leads to a fraudulent website designed to capture personal, valuable information. Once you’ve given up your information, it looks like it’s business as usual. However, the next day you may be shocked to find that your bank account is drained. Or, you can’t get into your email to let your friends know that, no, you aren’t stranded on an island in need of their immediate financial help.
For those running the scam, it’s a pretty low-stakes gambit that relies on people falling for a simple trick and handing over lucrative information. But for anyone who is the victim, it’s high stakes for sure. Learn how to spot these fakes below and protect yourself against phishing scams.
Signs That You May Have Received a Phishing Email
- Suspicious “from” address: Official emails about passwords and personal information are sent from official email addresses, not personal accounts. If the sender does not have an email address that is associated with the company, don’t believe it. Ne’er Do Wells often create email addresses that are close to a company name, but not quite right. For example, we recently warned everyone about emails that were allegedly from the Centers for Disease Control and Prevention, but the emails were from addresses that ended in
cdc-gov.organdcdcgov.org, neither of which is used by the CDC. A visit to the CDC site shows that their contact addresses all end withcdc.gov. - Odd tone: If something about the way an email is written seems “off,” listen to your gut. Generic greetings that don’t use your name, weird phrases, misspellings, and a call to urgent action that seems unnecessary are all tells that the email might not be authentic. Remember, even if you don’t have concrete proof, you can always contact the company through a phone number or email you’ve found somewhere trustworthy to make sure that it’s real.
- Links to fake websites:. That email, when done well, will take you to a convincing URL. Namecheck.com can test URLs for authenticity, and has a list of fake addresses as examples — like
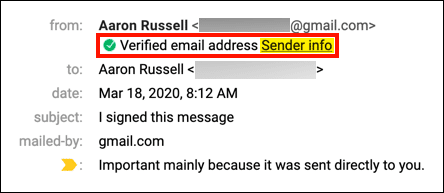
paypal-secure.onlineinstead ofpaypal.com. Some more well-crafted scams will take you to a page that is fraudulent but links to legitimate pages of the company. Look up the website yourself — don’t just click on links in emails. And make sure that any URL for a website where you are entering sensitive information is legitimate. - No digital signatures: If you are lucky enough to be working with a company that signs emails with S/MIME, that signature is proof of identity without even opening the email. However, it’s important to verify all info in emails and whether the certificate is a real, CA-issued S/MIME certificate, regardless.
If your email client supports S/MIME (and most do), it’s easy to check for and inspect a digital signature. Here’s how to do it in Gmail (for other clients, please check your vendor’s documentation):
1. Click the triangle to the right of the sender’s name to Show details.
The certificate is not trusted. For unsigned email, no certificate information will be displayed.

- No mention of known contact info: If an email that asks you to reset your password or give out information doesn’t contain additional information that you know is a way to contact the company or organization, be suspicious. Be very suspicious. Take a look at other emails you know have come from the organization, letters you have received in the mail, or the contact page on their website. Do you see the same info in the email you just got? Even if you don’t, just use the contacts you know to be trustworthy.
Signs You May Be on a Phishing Website
- Check the URL: Look at the page where you are submitting your information. Some fake URLs look straight-up fake. But, as noted above, many phishing pages have the trappings of the legitimate business that the fake is pretending to represent. So don’t be reassured if you can access the Chase homepage from the URL — carefully examine the page you are on. Is the company name spelled right? Is the top-level domain the same as the main page (
.comor.devs.orgor.gov, for example) and do the URLs start with the same prefix (e.g.https://)? One way to ensure that you are going to a real site is to use a previously-saved bookmark or searching for the site yourself with Google after closing and reopening your browser. - Popups: Use caution with sites that aggressively seek your password through pop-up windows. Some scams use popup windows over real sites, and use that as a way to earn your trust.
- Things don’t “feel” right: Give yourself some credit! We are able to pick up on little things that might not even register in our conscious mind. Scam websites often are slightly off in color, fonts and phrasing. Follow your heart if things don’t look right.
- No lock!: Web browsers show a closed lock for secure sites that use the HTTPS protocol, and legitimate sites just don’t ask for you to login without using HTTPS. If you see a warning or an unlocked lock in the URL toolbar of your browser, stop right there before offering up information. No lock, no login. And don’t ignore browser warnings — even though you may be so used to them that they don’t sound any internal alarms. Don’t dismiss warnings and only accept websites with browser-trusted certificates. Sadly, a lock is no longer an assurance in and of itself that a site is secure, as some phishers are now smart enough to use the HTTPS protocol, but the lack of HTTPS is a sure sign that you are on dangerous ground and should turn back.
How To Defeat Phishers
- Close your browser: Suspicious because of any of the above signs? Close your browser, and start anew without following any leading links.
- Enable two-factor authentication (2FA): Two-factor authentication simply means that you need more than one thing to access your sensitive information. One real world example is an ATM card — to get access to your bank account you need the physical card and the PIN. Online, two-factor authentication looks like a second step taken after a password is entered — sometimes this is a code sent to another device, or sometimes this is something unique to the user, like a fingerprint. The point is that having two required, disparate keys is much more secure and much harder to steal, so set up 2FA if it’s available on any website you log into regularly (like your bank’s).
- Check website certificates: While checking for security is no longer as easy as looking for HTTPS or the “green bar” that once was the standard in indicating Extended Validation (EV) certificates, it’s still a good move to look for these certificates, as we’ve explained previously. Many sites have made the choice to use cheap (or free) Domain Validated (DV) certificates that provide some assurances — you know your communication with the site is encrypted. However, DV certificates don’t provide the necessary assurance that you know who is actually operating the website. We’ve laid out how to find that info, for each browser, here.
- Stay protected with digital certificates from SSL.com: As the world becomes more digitally connected and more “meetings” take place online, it’s crucial to be able to verify identities online and avoid scams like phishing. SSL.com can help with:
- S/MIME, Document Signing, and Client Certificates: Fight phishing directly with digitally-signed email and documents, so your colleagues and customers know that that email or PDF is really from you. Client certificates add an extra authentication factor for remote workers and other users.
- SSL/TLS Certificates: Provide your visitors and customers assurance of your website’s identity and security.
- Code Signing Certificates: Assure customers that your downloadable code is from a trusted source and does not contain malware.
Finally, everyone can do their part and report phishing emails to spam@uce.gov and reportphishing@antiphishing.org, and give a heads up to organizations that are being impersonated, so they can protect others moving forward.